The Lync 2013 Edge Server is a bit different. It is actually an application gateway located in the companies perimeter network. It is not a domain member and it has two network interfaces. One network interface is connected to the internal network, the other network interface is connected to the external network. This interface can have a private IP address (and thus NAT’ed) or it can have an external IP address. Whenever possible I recommend using this configuration since it is less complex to troubleshoot. A second recommendation is to assign three different public IP addressesto the external network interface, used by the various Lync services (we’ll get back on this later on).
The first step of course is to install the server where Lync is going to be installed. This can be Windows 2008 R2 SP1 or Window Server 2012. The following prerequisite software needs to be installed:
- Windows Management Foundation 3.0 need to be installed on the server (includes Powershell 3.0). WMF 3.0 is part of Windows 2013, on Windows Server 2008 R2 SP1 it is a separate download: http://www.microsoft.com/en-us/download/details.aspx?id=34595
- The second prerequisite is .NET Framework 4.5 (part of Windows Server 2012) which can be downloaded here:http://msdn.microsoft.com/en-us/library/5a4x27ek(VS.110).aspx.
- Lync Server 2013 also requires the installation of Windows Identity Foundation in order to support server to server authentication scenarios. The Windows Identity Foundation can be downloaded here: http://go.microsoft.com/fwlink/p/?linkId=204657.
Note. For troubleshooting purposed I always install the Telnet Clientfeature on most Lync servers.
The Lync 2013 Edge server is not a domain joined server, but it does need a fully qualified domain name (FQDN). You can set this using the properties of the server.
After rebooting, logon to the server again and start the Lync server setup application to install the initial Lync server binaries (i.e. core components). When the core components are installed we can leave the server for now and continue with the Topology Builder on the Front-End server.
Topology Builder
Logon to the Front-End server and start the Topology Builder. Instead of creating a new topology download the topologyfrom an existing deployment and store the file on the local hard disk.
Expand the topology, right click the Edge node and select New Edge Pool. Follow the wizard and enter the FQDN of the pool and select the Multiple Computer Pool.
The next window is to select Edge features. You can use a single FQDN and IP address for all services, but then you need to use different ports (443/444/5061) but you can also use multiple URL’s with their own IP address, each using port 443. Since port 443 is open almost everywhere on the Internet this is my personal preference.
Select enable federation (port 5061)and when needed select Enable XMPP federation (port 5269)
New in Lync Server 2013 is the option to use IPv6 on the internal and the external interface so if you have an IPv6 infrastructure you can use it with Lync Server 2013!
Also on this page is the The external IP address of this Edge pool is translated by NAT optionif you don’t use public IP addresses on the external network interface. Since I’m using public IP address I do not check this option.
Enter the FQDN for the Access Edge Service, the Web Conferencing Edge Service and the A/V Edge Service. By default the ports 5061, 444 and 443 are used for these service but you can change them to 443 for all three services.
Follow the wizard and enter the internal IPv4 address and the internal FQDN of the Lync 2013 Edge server. Please note that the internal servers should be able to resolve this FQDN using the internal DNS! Follow the wizard and the three public IP addresses for the external FQDN’s.
The final steps is to connect the Edge Pool with the Front End pool which is called the Next Hop Pool in this case.
Similar to this is where the Edge Pool is ‘associated’ with the Front End pool, but now for external media traffic.
Click Finish to end the wizard, all information is now stored in the file on the local hard disk. The last step is to publish the information in the CMS. Right click the Central Site and select Publish.
Export the configuration
The Lync 2013 Edge server does not have access to the CMS since it is not a domain member. To initially get the information to the Edge server we have to export the configuration information, store it in a file and import this file in the Lync Edge server.
The only way to export the configuration information is to use the Lync Management Shell on the Front End Server. Enter the following command in the Lync Management Shell:
Export-CsConfiguration –File C:\temp\export.zip
Copy the file from the Front End Server to the Lync 2013 Edge server.
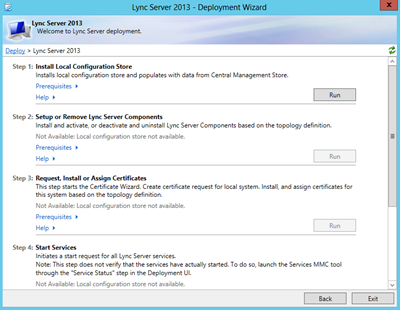
On the Lync 2013 Edge server start the Deployment Wizard and select Install or Update Lync Server System. In the wizard select Step 1: Install Local Configuration Store. The setup application determines it cannot access the CMS and automatically selects the Import from a file option. Enter the location of the file we just copied and click Nextto continue.
All software will automatically be installed, including SQL Express and all configuration information from the export file will be loaded in the SQL Express instance. This can take some time to complete.
When finished you can continue with Step 2: Setup or Remove Lync Server Components. This will install all Lync Server components that are needed, this information is read from the SQL Express instance that was installed in Step 1.
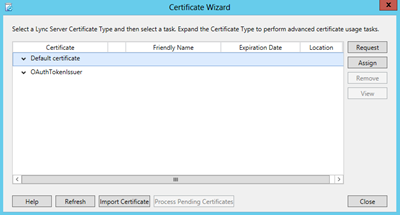
Step 3: Request, Install or Assign Certificatesis an important step. There are two certificates that need to be requested:
- Internal certificate – issued by the internal CA and used for securing internal communication between various servers;
- External certificate – issued by a (Microsoft certified) CA like Digicert. This certificate is used for securing external communication with external Lync clients or 3rd party Lync/OCS environment to setup federation. It is also used for server authentication.
Both certificates need to be requested using the offline mode, so create a .req file first and submit this to the appropriate CA (choose the option prepare the request now, but send it later (offline certificate request)).
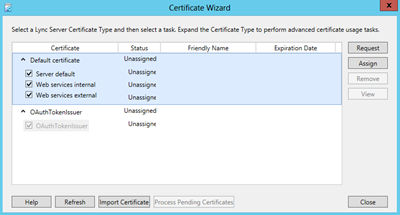
For the internal certificate, the pool FQDN (i.e. edgepool.exchangelabs.nl) is automatically used as the Common Name for the certificate, but you have to manually add the server FQDN to the request file. Once the certificate is issued by the internal CA and you have it stored on the local hard disk of the Lync Edge server you can use the Import Certificatebutton to import the SSL certificate in the certificate store of the server.
After importing use the Assignbutton to assign the certificate to the Lync Edge services.
If you don’t see the certificate most likely the root certificate of the internal CA is not installed on the Lync Edge server causing the server not to trust the certificate. If so, import the root cert certificate of the internal CA on the Lync server and try again.
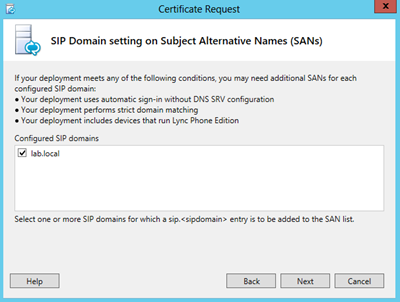
Repeat the same steps for requesting the external SSL certificate. The three server names (access.exchangelabs.nl, webconf.exchangelabs.nl and av.exchangelabs.nl) that were entered in the Topology Builder are prepopulated in the wizard. This should be sufficient, but I always add the pool FQDN (edgepool.exchangelabs.nl) to the certificate as well.
Store the .req file on the local hard disk of the Lync Edge server and request the certificate at your preferred SSL vendor. Personally I work a lot with Digicert, they are not too expensive, are supported by most clients (and UC Certificated by Microsoft) and their 247×7 support is great.
When requesting the certificate select the Microsoft Lync Server 2013 in the left pane and add the contents of the .req file in the right pane.
The CA will automatically retrieve the servers names and put these in the certificate.
When the request is submitted it’s just a matter of time before the certificate is issued and returned to use (via e-mail or via the Digicert portal). Store the certificate on the local hard disk of the Lync Edge server and import the certificate on the Lync Edge server using the Import Certificatebutton in the Deployment Wizard.
Use the Assignbutton to assign the Digicert certificate to the external Lync Services.
Use Step 4: Start Services to start all Lync services on this server and use Step 5: Service Status to check if all Lync services have started successfully.
The last step is to add two service records (SRV) to the public DNS so Lync clients that try to logon via the Internet can find the Lync 2013 Edge server and other Lync and/or OCS environment that you want to federate with can find the Lync 2013 Edge server.
The following SRV records need to be created:
_sip._tls.exchangelabs.nl 0 0 443 access.exchangelabs.nl _sipfederationtls._tcp.exchangelabs.nl 0 0 5061 access.exchangelabs.nl
Where access.exchangelabs.nl is the FQDN of the Lync 2013 Edge server.
You can check the SRV records using the NSLOOKUP utility:
Easy to forget… you have to enable external access in the Lync Control Panel (by default this is disabled!). Logon to the Lync 2013 Front End Server and open the Lync Control Panel.
In the left navigation menu select Federation and External Access. In the top menu select External Access Policy and double click the Global Policy. Click Committo save all changes.
After committing select Access Edge Configuration and double click the Global Policy to open it. Check the Enable Federation and Public IM connectivity, check Enable partner domain discover and check Enable remote user access. If needed you can check the other options as well. Click Commit to save all changes.
The changes are saved into the CMS database but need some time to replicate to other Lync servers. In a multi location deployment with servers in multiple countries (check about a Survivable Brach Appliance or SBA) this can take some time. If you click Topologyin the left hand menu you can check the replication status.
If everything is up-and-running and synchronized you can (try to) logon externally via the Internet. The Lync client will automatically retrieve the correct server (access.exchangelabs.nl) and logon. And if you have port 5061 the federation will work as well.
In the client screenshot the Jaap Wesselius contact is on an external Lync (2010) environment with federation enabled.
My next blog will be about firewall ports, the Mediation Server and a SIP trunk, configuring TMG or reverse proxy through an F5 load balancer. I’m not sure which one to do next, so stay tuned